Just one simple email can halt all the production in your company, potentially causing the loss of millions of EUR/US$ per day – that’s serious!
Phishing attacks, generally via email also via SMS, one of the oldest and most effective forms of cyberattack, are becoming increasingly sophisticated. Even experienced users, including cybersecurity experts, can be tricked. Why is that?
In today’s criminal landscape, some rogue organizations or governments employ psychologists and psychiatrists to craft highly convincing emails and links, and even create mock identical websites that mimic your company’s website.
For many, identifying phishing emails – especially those with hidden or deceptive links, often through text or a button – can be challenging. This article provides a quick guide and an example on how to spot these threats:
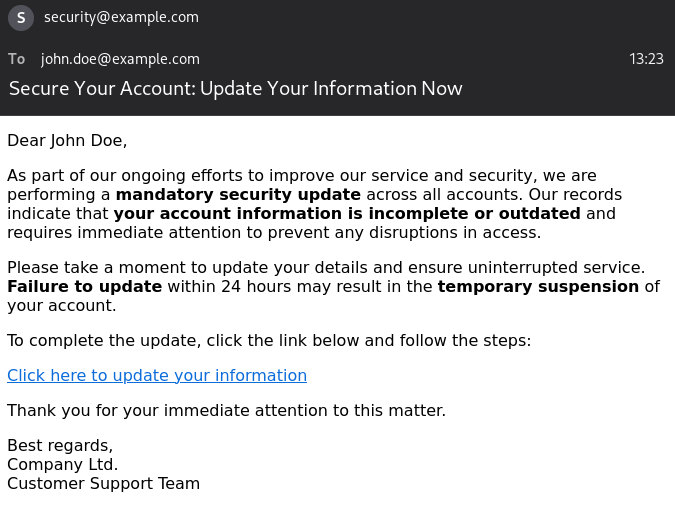
1. Start at the top: Look for Suspicious Sender Information
Phishing emails often come from addresses that seem familiar but have subtle anomalies. Always check the sender’s email carefully:
• Misspelled company names.
• Generic email domains like @gmail.com instead of company-specific domains, as legitimate companies should use their own domain.
• “Undisclosed recipients” or other oddities in the recipient field.
2. Examine the Email Content for Urgency or Threats
Phishing emails often create a false sense of urgency, for instance “Your account will be locked or suspended!”. Legitimate companies don’t pressure users this way. If the message seems too urgent or threatening, be skeptical and call the sender directly – taking a few minutes to verify can save you much more time in the long run, and possibly even prevent legal issues.
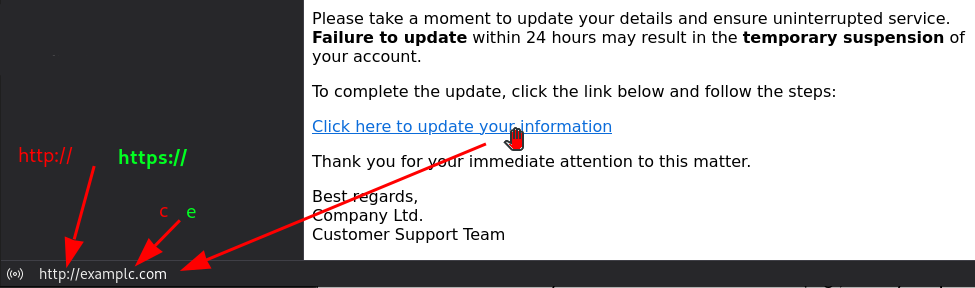
3. Hover Over Links Without Clicking
A key sign of phishing emails is the presence of misleading links. Hover your mouse pointer over any link (without clicking) to check where it actually leads – a bubble will pop up with the address or appears in the status bar – see picture (look at the beginning, the domain name “example.com”, and not the rest behind). Look for:
• Discrepancies between the visible link and its destination.
• Misspelled domain names or extra characters in the URL.
• Shortened links, which are often used to disguise malicious destinations.
• If your web browser’s security is disabled, check for the “https://” (see picture) prefix in the URL to ensure the connection is secure.
4. Look for Generic Greetings
Phishing emails often use generic phrases like “Dear Customer” or “Hello Dear” instead of addressing you by name. Genuine emails from companies you’ve dealt with will usually address you by your full name or username.
5. Verify with the Source Directly
If an email asks you to take immediate action (e.g., reset your password, make a payment), go directly to the company’s official website or contact their support team by phone. Never trust the links in the email itself.
6. Check for Spelling and Grammar Errors
Many phishing emails are poorly written, with awkward phrasing, missing punctuation, or spelling mistakes. Legitimate companies usually proofread their emails carefully. In case of doubt, call the sender directly to confirm (sometimes the official language isn’t the sender’s mother tongue).
Conclusion
Recognizing phishing emails requires vigilance, but by following these simple steps, you can protect yourself from falling victim to these types of attacks.
Don’t dismiss the narratives like, “he (she) is overdramatic…”. It’s better to be a bit overdramatic than to be sorry afterward.
When in doubt, don’t click any links, and always verify through official channels.
New Threats!
There’s now a new threat – although not entirely new but making a comeback – called snail mail (physical mail) phishing or scams:
Some months ago, I received a “letter” claiming to be from my bank. How did I recognize it as a scam? As simple as it was, the stamp! Everything else about the letter was identical to the official correspondence my bank typically sends. This highlights the importance of scrutinizing even traditional communication channels, as scammers are increasingly adept at mimicking legitimate mail, telephone calls, and messaging.
As a side note, I don’t even use traditional telephone calls for secure or highly private communications, instead, I rely on one of the most secure messaging apps.
But this is a topic for a future article!
